Every year, the world discards millions of tons of electronic devices. Behind that volume lies a striking truth: many of those devices still hold data. A misplaced hard drive, or one “recycled” without proper erasure, can turn into a data breach scenario.
That’s where ITAD asset disposal and recycling comes in. It goes far beyond traditional electronics recycling. It brings together rigorous security, auditability, value recovery, and environmental care across the full disposition process.
In this post, you’ll learn:
- How ITAD differs from generic recycling
- The mechanisms behind ITAD’s methods of data sanitization and reuse
- How to decide when to use ITAD vs recycling
- Common trade-offs, implementation tips, and vendor considerations
- Real cases where ITAD made a difference
- FAQs that clarify core concepts
Let’s begin by defining the landscape.
What is ITAD and how it works
Definition and scope
ITAD (Information Technology Asset Disposition) is a comprehensive process for retiring technology assets in a way that protects sensitive data, maximizes residual value, and reduces environmental impact. It typically spans from pickup to final disposition, under a safeguarded, traceable chain of custody.
The core components of ITAD include:
- Data sanitization (wiping, degaussing, shredding)
- Refurbishment and remarketing
- Fallback recycling for non-recoverable components
- Audit, certification, and reporting
ITAD is designed to fit within your broader life cycle of IT assets—making sure that security and value recovery are integrated, not an afterthought.
Typical methods
Some of the most common techniques used in ITAD include:
- Wiping/software erasure — Overwriting data to meet standards like NIST 800-88
- Degaussing — Erasing magnetic media using strong magnetic fields
- Drive shredding/physical destruction — Ensuring drives are irrecoverable
- Testing and refurbishment — Evaluating which assets can be reused
The ITAD provider matches method to risk, asset type, and compliance needs.
Role in asset lifecycle management
Within a mature ITAD process, disposal is just one phase. ITAD ties into provisioning, usage, refresh cycles, and end-of-life planning, ensuring that your hardware is tracked, secured, and optimized across its full journey.
What is traditional/e-waste recycling
Definition and process
Traditional e-waste recycling focuses on recovering raw materials from obsolete electronics. The process often includes:
- Collection and aggregation
- Disassembly and separation of components
- Mechanical shredding, sorting, smelting
- Material recovery (metals, plastics, rare elements)
It treats devices more as sources of materials than as functioning units.
Focus and limitations
While recycling recovers materials, it typically does not preserve device functionality, nor does it center on data security or residual value. It’s agnostic about the operating condition of devices.
The steps are often: dismantle → sort → shredding → smelting. Data security is an afterthought or handled by destruction only, not integrated refurbishment.
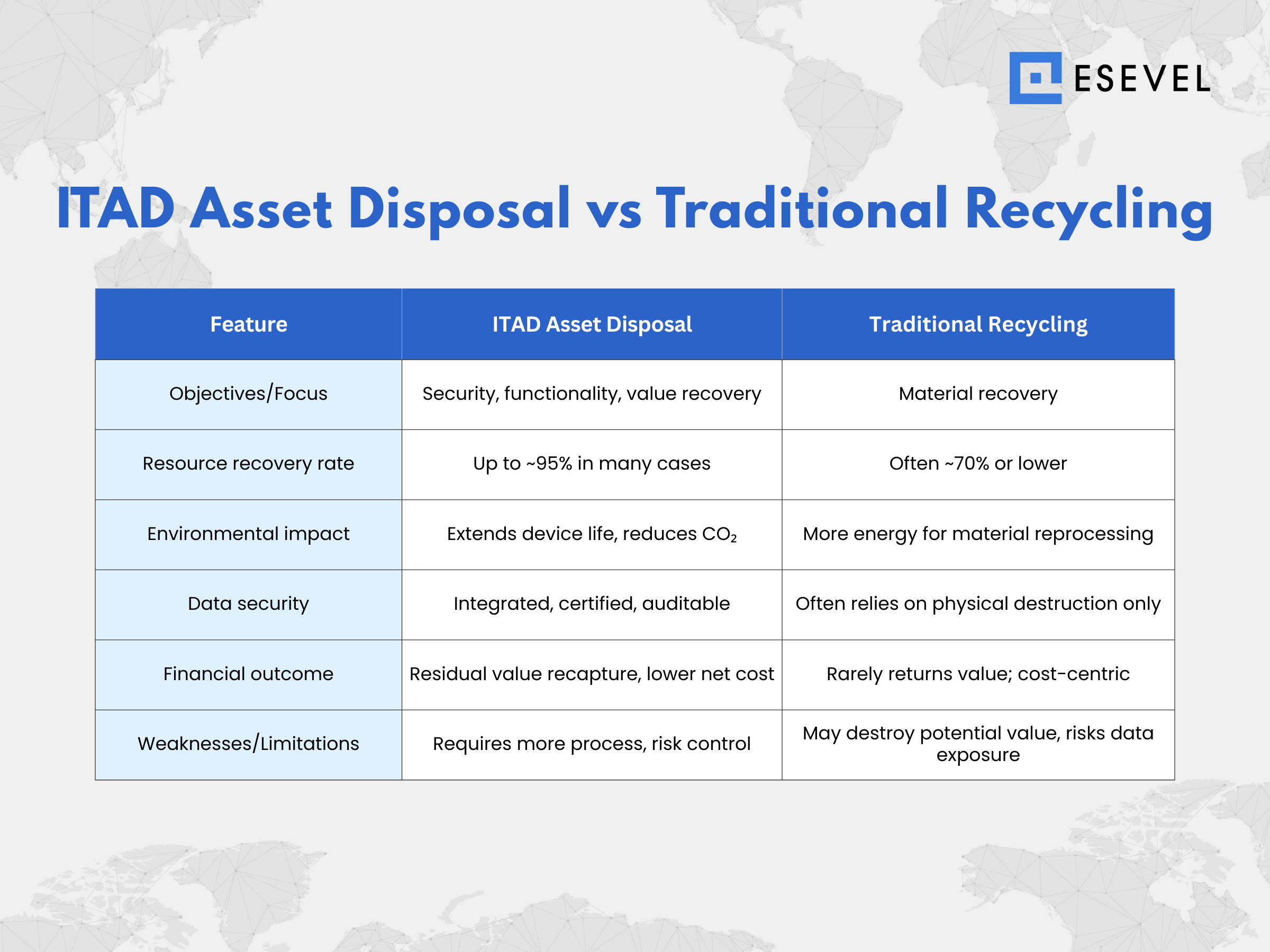
In many evaluations, ITAD achieves up to 95% resource recovery, while traditional recycling may reach ~70%. Recycling recovers raw materials but discards functionality; ITAD tries to retain it.
ITAD also typically reduces environmental impact compared to raw recycling due to lower energy in refurbishment and less waste.
When to use ITAD vs recycling (decision guide)
Choosing which approach to take depends on multiple criteria. Here’s a decision framework:
Criteria to consider
- Device condition & functionality — If the device still works, ITAD’s refurbishment path yields more value.
- Data sensitivity — Highly sensitive systems demand stronger methods (e.g. shredding) which lean ITAD.
- Resale/reuse potential — If market demand exists, ITAD pays off.
- Regulatory/compliance obligations — Some laws require auditable destruction.
- Total cost vs risk trade-off — ITAD has higher process costs but lower breach risk.
Examples
- For a fully obsolete server cluster containing sensitive data, choose ITAD with drive shredding and certified reporting.
- For broken peripheral items with no resale viability (e.g. old cables, plastic parts), recycling is acceptable as fallback.
- Use a hybrid approach: first run ITAD workflow; then recycle residual scrap.
Because regulatory environments are tightening, many firms adopt ITAD-first posture: attempt recovery, fallback to recycling.
Challenges, trade-offs, and implementation tips
Even with clear advantages, implementing ITAD asset disposal and recycling brings complexity.
Cost & process overhead
ITAD demands more steps, logistics, audit, and vendor scrutiny. The incremental cost can deter small operations.
Vendor capacity and geography
Not all providers can support remote locations, data center decommissioning, or region-specific regulations.
Chain-of-custody and audit ownership
Your internal system must align with the vendor’s tracking. Gaps create audit risk.
Legacy/nonstandard hardware
Devices like embedded systems, smart appliances, or legacy storage need specialist handling.
Implementation strategies
- Start with pilot runs to validate processes
- Segment assets by risk/usability class
- Audit vendors regularly
- Standardize workflows across regions
Case studies & examples
Great Forest: $10M savings with smarter ITAD
Great Forest reports that one client saved over $10 million by applying specialized ITAD and e-waste services to 12,000 servers across 15,000 branches. They emphasize ITAD’s combined focus on resale, secure erasure, and environmental impact.
Rica Recycling’s circular commitment
Rica Recycling enforces a 100% landfill-free policy, aligning their recycling and ITAD operations under circular economy principles. They combine secure destruction with asset recovery, making recycling a component of ITAD, not the whole.
Savings and risk avoidance example
In a recent ITAD project, a firm avoided a $120K penalty by properly executing secure decommissioning and data destruction for their data center assets. That outcome shows how ITAD is not just about disposal—it’s about risk management.
Strategic positioning for the future
To summarize:
- ITAD asset disposal and recycling blends security, value recovery, and environmental responsibility.
- It outperforms pure recycling when data risk, resale value, or compliance requirements are in play.
- The best practice is to optimize for ITAD first, and fall back to recycling when needed.
- As regulatory expectations expand (e.g. mandatory sustainability reporting, due diligence mandates), the margin of error narrows.
If you’re still relying primarily on generic recyclers, it’s time to elevate your approach. Audit your disposal system, introduce ITAD workflows, and partner with certified itad services that handle decommissioning, chain-of-custody, and secure destruction.
Esevel can help you design and manage an ITAD + recycling strategy that fits your tech lifecycle—ensuring devices are retired safely, securely, and sustainably.
FAQs
What does “itad asset disposal and recycling” really mean?
It refers to a combined approach where technology is first processed under a secure ITAD workflow (sanitize, recover, remarket) and then residual parts are recycled.
Can traditional recycling ever replace ITAD?
Only in low-risk, non-data-bearing, fully obsolete cases. But for data-bearing, high-value devices, recycling alone fails to protect sensitive information.
Will ITAD always cost more than recycling?
Often yes, but the extra cost is justified by risk reduction, compliance, and residual value. Sometimes the net cost is even lower when resale is successful.
How to measure environmental benefit of ITAD vs recycling?
Compare resource recovery rates (ITAD up to 95% vs ~70% recycling), carbon emissions saved, landfill avoidance, and reuse metrics.
What criteria should I use to choose a vendor or method?
Data sensitivity, device condition, resale potential, regulatory needs, geographic coverage, and vendor certifications.
What are common pitfalls to avoid?
Ignoring chain-of-custody, using uncertified vendors, failing to audit, overestimating resale value, mixing high-risk and low-risk assets in one process.







